How can CSV files be affected?
Well, technically CSV files are text files - the purpose of a CSV is in its name - Comma Separated Values. The issue is actually a combination of spreadsheet software interpreting values as formulas (thus no longer treating values as plain text) and the tendency of users to ignore security prompts - or to agree to terms and conditions without scrolling through :-)
Basically, spreadsheet software such as Microsoft Excel will treat values differently if they start with special characters, such as:
- Equals to =
- Plus sign +
- Minus sign -
- At @
Slightly more info on this here.
How does this affect you?
There are some steps needed before the injection is executed:
- Your forms must be publicly accessible;
- Data must be saved in the database;
- One of the forms must be submitted (successfully) - the payload (which for obvious reasons will not be shown here in its entirety) will be sent in a random field of the form.
- An administrator would have to login into the backend and export a CSV from the submissions area.
- The CSV will now contain a value that starts with a special character - for example,
=cmd
- When the CSV is opened in a spreadsheet software, Microsoft Excel for example, the user is presented with a security warning:
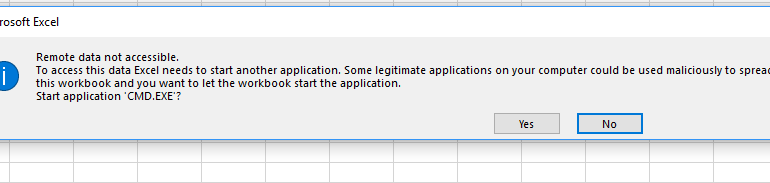
- The injection is successful by leveraging user's perception of what's happening - since it's from your own (or known) website, the data must be valid and the warning message is most likely a false positive. In this case, it is not. The user will have to click on 'Yes' to start the application. What the application does and how it's downloaded on the user's disk is an entirely different matter.
Is this vulnerability actively exploited?
As far as we know, at the time of this writing, no. The reason for this is that it's not a 0-day exploit and it requires several prerequisites for it to be successful.
Extensions affected
- RSForm! Pro older than 2.2.1
- RSEvents! Pro older than 1.12.3
- RSEvents! Pro Cart Plugin older than 1.1.15
- RSMembership! older than 1.22.11
- RSDirectory! older than 1.9.11
Bottom line
Pay attention to security messages or prompts - they're there for a reason.
